Looking to bolster your DNS Security with DMARC and SPF? This guide will show you how to protect your business email system from spoofing and phishing attacks.
Contents
The Challenge: Ensuring DNS Security and Combating Email Vulnerabilities
Your Domain Name System (DNS) security protocols like DMARC (Domain-based Message Authentication, Reporting, and Conformance) and SPF (Sender Policy Framework) are crucial for safeguarding your business against email vulnerabilities.
Why DNS Security Matters
Without proper DNS security, your business is susceptible to email spoofing and phishing attacks. This could lead to unauthorized access to sensitive information, financial loss, and a tarnished domain reputation.
Implementing DMARC and SPF for Optimal DNS Security

DMARC and SPF offer a robust defense for your email system by authenticating the messages sent from your domain and providing a policy for handling messages that fail authentication.
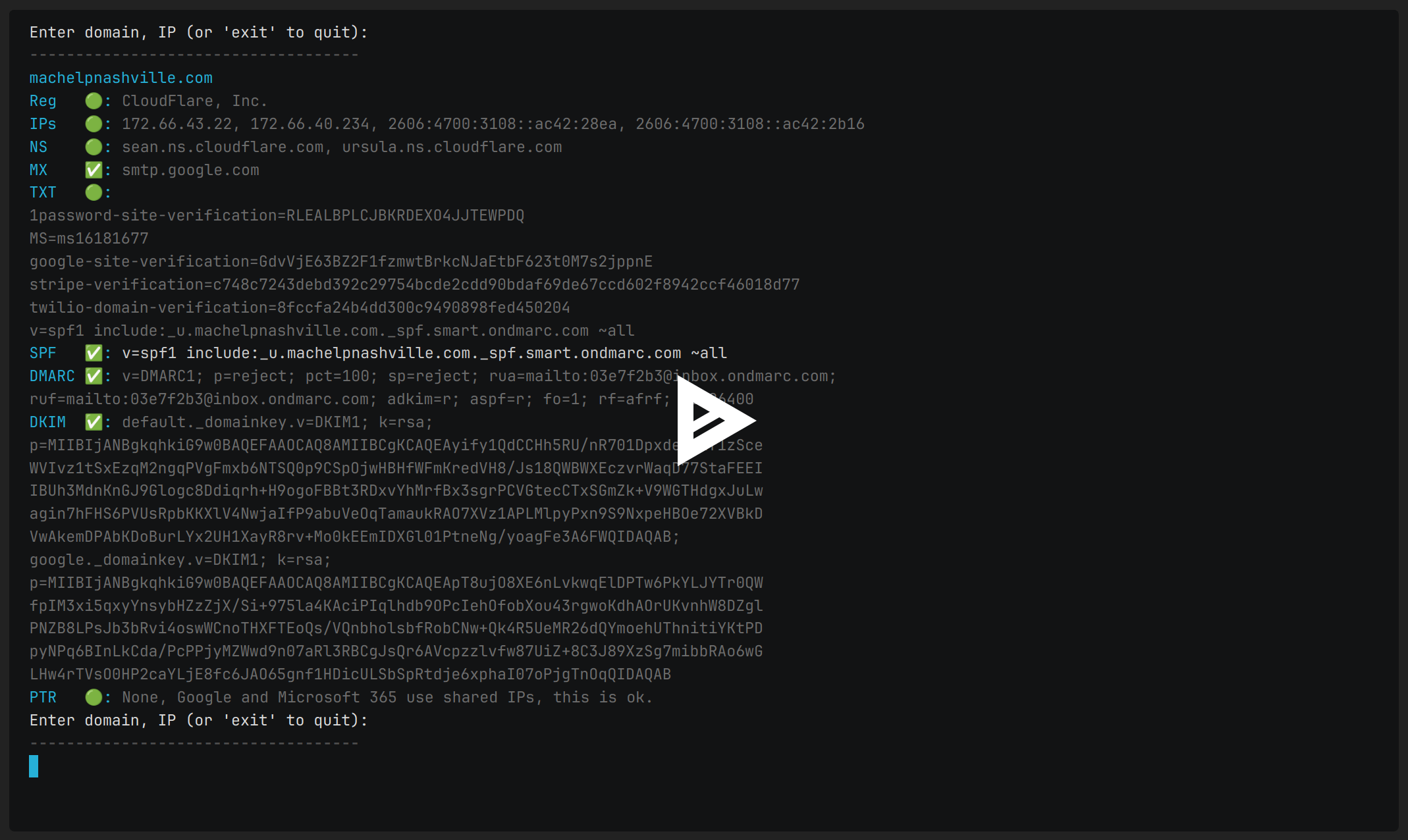
Sample DMARC and SPF Records: Key Elements of DNS Security
Enter domain, IP (or 'exit' to quit):
------------------------------------
cisa.gov
Reg 🟡: Unknown or Classified
IPs 🟢: 23.5.154.88, 2600:1402:b800:d89::447a, 2600:1402:b800:d84::447a
NS 🟢: a22-66.akam.net, a1-91.akam.net, a7-64.akam.net, a16-67.akam.net, a9-66.akam.net, a8-65.akam.net
MX ✅: mxb-00376703.gslb.gpphosted.com, mxa-00376703.gslb.gpphosted.com
TXT 🟢:
google-site-verification=BNRBfY90BM54Mf_pgL4Eg07IkwbGvq5nsdZCOYadDlM
MS=ms41452370
google-site-verification=wsLVyeZYgv0NLikdmfm2m3XPP-986Ylo8XxUkrjIOvA
MS=ms36056523
MS=ms53160703
v=spf1 include:spf.dhs.gov include:spf.protection.outlook.com include:spf-00376703.gpphosted.com -all
SPF ✅: v=spf1 include:spf.dhs.gov include:spf.protection.outlook.com include:spf-00376703.gpphosted.com -all
DMARC ✅: v=DMARC1; p=reject; pct=100; rua=mailto:DMARC@hq.dhs.gov,
mailto:reports@dmarc.cyber.dhs.gov
DKIM ✅: selector1._domainkey.v=DKIM1; k=rsa;
p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAv32BRAJaAOsxAp31ZqQwd7RYfbYowvb3F7
q8WQEyasI6w7Gm0bxPW57TFM04fM5flf1PYyCDSa3ckQzSQLYmMx9HiXYJYF1Dpk9PnjTarbdR9mm9fc
iBXT2pTFNJw+SRMH3NRrbkefv8GqqLdJotgCl2vWoyRlfKCANCFq5Bbq4qaztXqU/cHRurG8ZVSF7Zrh
4EBKvpzAyIisrf2g2Gky+vO4LTMrgZeNnA/OyHmWmvlUC58e06jBLSysYyh19O4MiU5eUhuT7MYTLWz6
IOl4PaT9HkmM0rH/fgcGSYc8ajCsrvxYA8LgoWR9IzYq5vYzDWLxSo/J0c+6pVWQIDAQAB;
PTR ✅: a23-5-154-88.deploy.static.akamaitechnologies.com,
g2600-1402-b800-0d84-0000-0000-0000-447a.deploy.static.akamaitechnologies.com,
g2600-1402-b800-0d89-0000-0000-0000-447a.deploy.static.akamaitechnologies.com
Enter domain, IP (or 'exit' to quit):
------------------------------------
Notice that the policy is set to reject 100% of unauthorized messages.
Mac Help Nashville, Inc. proudly participates in CISA’s Cyber Hygiene program for critical cyber infrastructure.
We have learned so much from our assigned feds, and I love experiencing the yearly red team,
where top hackers at CISA hack your company and show you what they could steal and how to prevent it.
One cool macOS security tool we installed that gave our fed, who was red-teaming us the most trouble, was LuLu by Objective See.
It kept ratting out and stopping the CISA rats! haha
Common SPF Misconceptions
Contrary to some misunderstandings, the -all tag in an SPF record does not prevent internal users from sending or receiving emails. Rather, it mandates that only explicitly allowed sources can send emails on behalf of the domain. This means email newsletters that are sent with Mailchimp or Zendesk, for example, will not be able to successfully send emails that arrive from your domain without having an “include:” entry. So you allow them with an “include:” entry.
Alternate Viewpoints
Mail Hardener recommends using SPF Softfail over Fail for better compatibility and fewer delivery issues.
Scientific Backing
According to RFC 7489, Section 10.1, the use of -all can cause messages to be rejected before DMARC processing, something operators should be aware of.
Practical Tools for DNS Security
You can use our free open-source utility, dns-scout, to easily test domain records from your MacOS or Linux terminal.
We also recommend using securitytrails.com for tracking DNS changes and OnDmarc.com for dynamic SPF records.
Step-by-Step Guide to Setting Up DMARC and SPF
If you’re new to DNS security, here’s a simple checklist to help you set up DMARC and SPF:
- Verify domain ownership
a. The Registrar is where the yearly bill is paid (and could also be the place to edit DNS records)
b. The NS server records tell you where to edit the DNS records; they are the DNS hosts. - Create an SPF record listing authorized email servers
The two most typical are:
a. v=spf1 include:_spf.google.com ~all
b. v=spf1 include:spf.protection.outlook.com -all
c. note the two above records do not have entries for other things that may need to send email as your domain. - Set up a DMARC policy.
a. Start HERE - Test the setup using dns-scout or web-browser-based securitytrails.com
If you are using DNS-Scout, keep adjusting until you see all the fields correct and green. - Monitor and adjust as needed
Common Pitfalls to Avoid
When setting up DMARC and SPF, watch out for these common mistakes:
- Incorrectly formatted DNS records
- Not updating DNS records after changing email providers
- Setting overly strict policies initially
FAQs: Your DNS Security Questions Answered
- Can I set up DMARC and SPF myself?
Yes, but it’s advisable to consult a DNS security expert. - What happens if I don’t set up DMARC or SPF?
Your email system will be more susceptible to phishing and spoofing attacks.
Additional Security Measures
Beyond email security, a Brand Indicators for Message Identification (BIMI) record can validate your company’s logo on platforms like Gmail. Learn how to set it up at bimigroup.org.
Statistical Urgency
In 2022, business losses exceeded $10.3 billion. due to email scams, according to the FBI’s 2022 Internet Crime Report. This underlines the importance of securing your email infrastructure.
Conclusion
Securing your domain and email system is not just a technical requirement but a business imperative. Implementing DMARC, SPF, and DKIM can significantly reduce the risk of email spoofing and phishing attacks. Don’t be a statistic—take action today.
Wonder why “null” images replace your logo in Mac Mail and iOS email signatures? See our article: How to get rid of those missing image errors “null” in Mac Mail and iOS email signatures.